Cybersecurity refers to measures taken to protect against criminal or unauthorized use of data. The use of cybersecurity can help mitigate potential data breaches, identity theft and loss of sensitive information.
Table of Content

1. What is the Difference Between HTTP and HTTPS?
- HTTP - stands for Hypertext Transfer Protocol. This protocol is used to send data between your web browser and a website.
- HTTPS - stands for Hypertext Transfer Protocol Secure. This protocol is used to encrypt the data sent between your web browser and a website.
- Sensitive information (financial, member info, login credentials) should only be entered or accessed using HTTPS websites.
- A website using HTTPS does NOT mean it is legitimate and safe to use! It only indicates the website employs encryption to protect any sensitive information you send or receive from the website. HTTPS can be easily implemented by any website - this includes malicious sites..
- Most web browsers today will provide you with a visual aid, such as a padlock icon in the address bar, to indicate if the website you are connected to is using HTTPS. The URL will also begin with https://
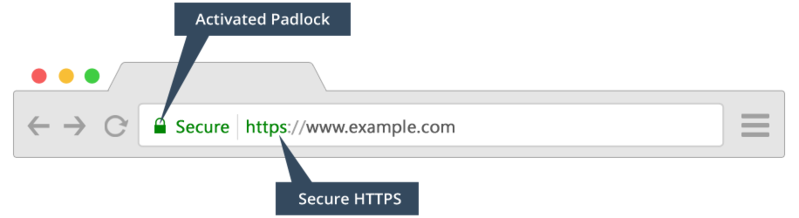
2. What are SSL Certificates?
An SSL certificate is the mechanism used by a website to encrypt sensitive information that you send or receive. Sensitive information includes your login credentials, bank account numbers, and you home address. Additionally, SSL certificates help verify the identity of a website, as well as provide the unique encryption keys used to encrypt and decrypt information sent between your computer and the website.
- SSL Certificates are issued by a Certification Authority to a specific entity.
- Verifies the identity of the website it is issued to.
- An SSL Certificate issued to Microsoft cannot be used by Apple. Attempting to use another entities certificate would produce an error saying the website is "Untrusted" or "Unsecure".
- A valid SSL Certificate only proves the entities is who they say they say they are. This does NOT prove their legitimacy!
You can view information about an SSL Certificate by clicking on the padlock in your web browser.
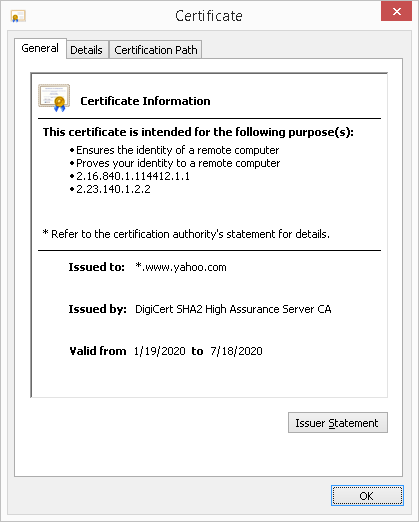
- Verify the website the certificate is issued to.
- Who the issuing Certificate Authority is.
- Dates the certificate is valid from.
3. What is Encryption?
Encryption is the process of modifying information to make it human unreadable, until the encryption process is reversed to make it readable again.
Unencrypted Text (Plain Text Data)
Mr. Wonderful, please find attached our revenue and profit statement for the last fiscal year. This is confidential information and you are bound to our non-disclosure agreement.
Encrypted Text (Cipher Data)
NTU4T244QStMYmxzMDN0K0kybE5TMldGSkx2N1I3ODM5cmk5SzVMZ0FGUGNYY1pYSFk2dXQ2TGtVOTM2SkVGOXRidHc1dDRtRThIUzg0emtJcXJYNVBSNEVyQzBtTUNiaUVGQm45SmZ4TnQ1OUM2b1kzckh0cEpyZGo1bVhBM0U5aDVQeW00R0hLTW8xSFRmMEF4MWVBTDJPL2Z6NlZSQmJpenUyZitaVlVjazFQQ1JCNTFqZHNUUmVtYngzWnpvd0dPa0VZMzV0ZVAzL3FJNUV5OUVkU09pL1NCd25INndycGo1VXJGV0ZQT2dlN0FEMDAzZGRreGxQRTNMbGsxcDo6eLlb2msVInbdA7X4u9FV2g==
- Encryption is used to send information securely over the Internet.
- Encryption can also be used to store sensitive information.
- If an encrypted document is stolen, it is rendered useless unless the person has the key or password to decrypt its content.
- Information and file validation is also a primary use of encryption.
- A cryptographic "hash" (digital fingerprint) is used to check the integrity of data. It helps determine if a file is a legitimate, unmodified version of the original file.
- Hashes can also be used for authentication, such as verifying passwords
- Online Hash Generator Tool - https://www.miraclesalad.com/webtools/md5.php
4. What is Malware?
Malware is software that is intended to perform malicious actions on a device. The word 'malware' is derived from the words 'malicious' and 'software.' There are many different classifications of malware:
- Virus - Malware that replicates itself when executed by modifying code in other computer programs on your system. Used to bring systems offline by corrupting data and causing system failure.
- Worms - Similar to a virus, spreads throughout devices corrupting data and bringing network systems offline. Unlike a virus, worms can be spread without being executed by the user.
- Spyware - Malware that is used to spy on the user. It can record your keystrokes and activities and use this information to steal passwords and sensitive files.
- Ransomware - Malware that encrypts all of your personal files and holds them hostage. The password to unencrypt your files may be provided to you after you have paid a ransom. The ransom payment is usually demanded in the form of cryptocurrency, such as Bitcoin. Unlikely wire transfers or checks that leaves a documented trail, cryptocurrency cannot be traced.
- Adware - Malware designed to expose you to unwanted, potentially malicious advertising. Adware can also redirect your browser searches to product promotions or even phishing websites.
- Fake/Virus Alert Scam - Malicious websites or advertisements may redirect your web browser to a fake "virus alert" page. This page produces warnings saying your computer is infected, and gives you a number to call. If called they will attempt to have you give them control of your device, as well as send them money for their virus removal "services".
Common Sources of Malware
Malware can be present on any website or software that contains malicious code or downloads. There are a few common sources where malware is the most prevalent:
- Spam emails
- Gambling websites
- Sites offering free games and software
- Adware is the most common type of malware from these sites
- Adult websites
- Embedded advertisements (banner ads, popups)
- Unpatched software vulnerabilities
- Ensure your software and operating system have the most up to date patches installed.
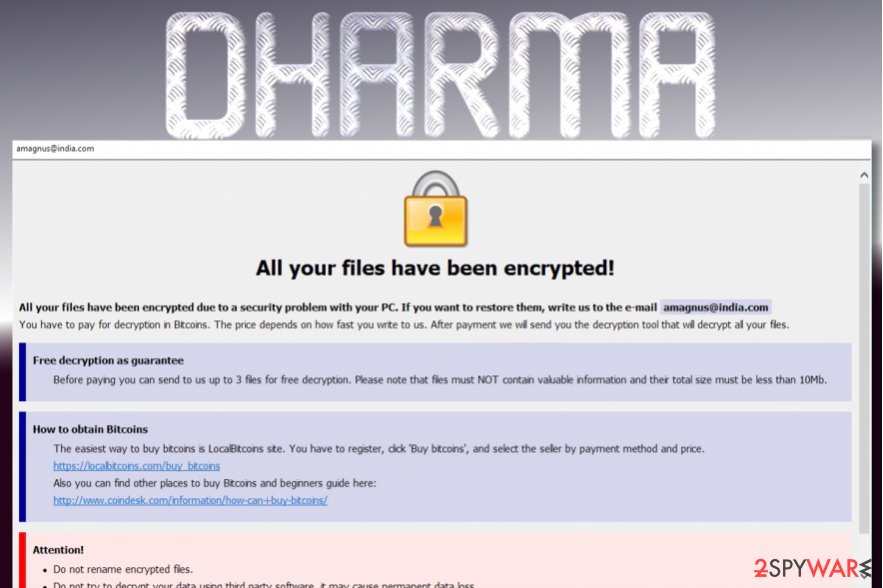
Example of Ransomware
If you happen to suffer a ransomware attack, your pictures, documents, spreadsheets, and many other important files will be encrypted by the perpetrator rendering them inaccessible to you. A ransom note, such as the example illustrated below, is presented to you demanding payment in exchange for the decryption key (i.e., password) to decrypt your files.
Real-World Ransomware Incidents
In January 2018, Hancock Health suffered a ransomware attack and had to paid hackers 4 Bitcoins (totaling $55,000 at the time) to unlock their computer systems. Read more about this ransomware attack at https://www.zdnet.com/article/us-hospital-pays-55000-to-ransomware-operators/
A Dallas police department was infected with a ransomware that encrypted over 8 years of digital evidence, including one active criminal case. They were able to recover much of their data, without paying the $4,000 ransom, using data backups they had created. Read more about this ransomware attack at https://www.bankinfosecurity.com/ransomware-freezes-eight-years-police-evidence-a-9664
Example of Virus Alert Scam
A common type of an virus alert scam is a web browser under guise of Microsoft Support. This notification attempts to fool people into thinking that Microsoft has detected a virus on their computer and can offer assistance in removing it. In reality, it is just a scam - there is no virus - it is using scare-tactic to lure you into calling the scammer's toll-free number. A screenshot example of this virus alert scam is shown below.
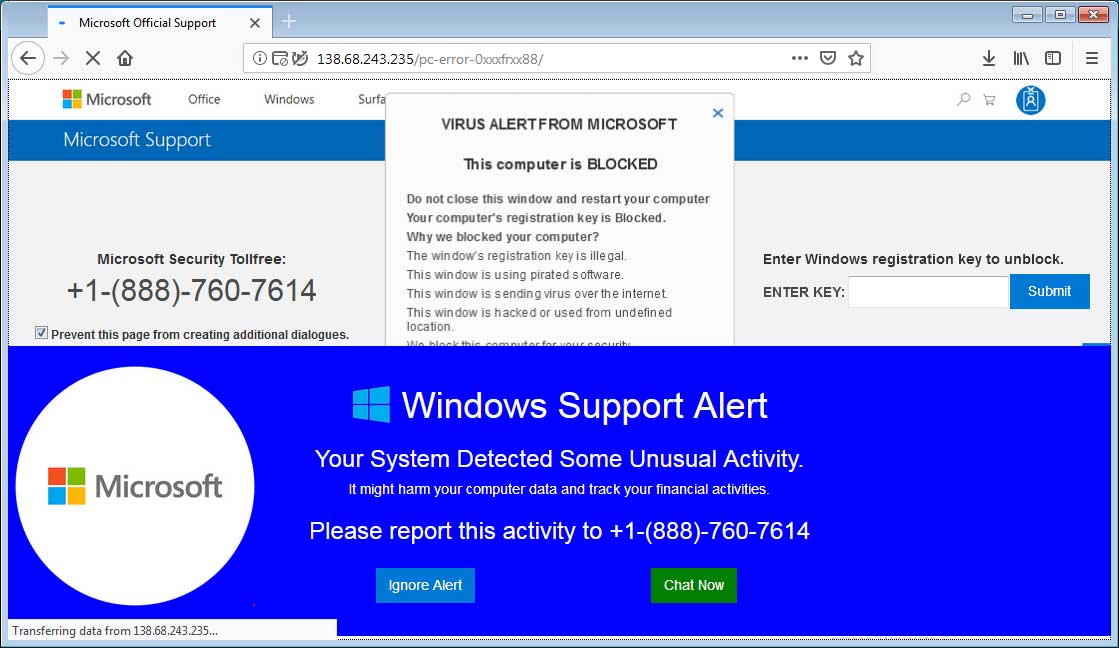
If you do fall victim to this scam, a number of potential things can happen:
- You lose money paying the scammer to "remove" a non-existence virus.
- You potentially can give the scammer remote access to your computer.
- Scammer can install a remote access tool that can give them persistent covert access to your computer.
- Scammer can remotely stream screenshots of your computer activities.
- Your sensitive and important files can be stolen (potential identity theft).
- Ransomware can be implanted onto your computer.
- Keylogger tool can be installed to capture your keystrokes (such as when you log in to your bank websites).
To learn more about this Microsoft virus alert scam, please visit www.bleepingcomputer.com.
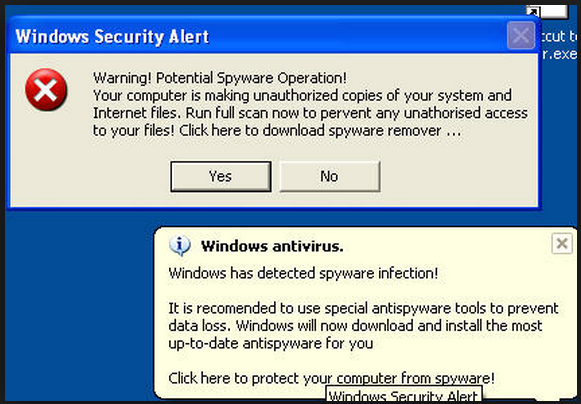
Example of Fake Alert Popups and Messages
- Malicious website can create alert popups.
- The dialog buttons on many of these are fake.
- Pressing "Cancel", "No" or the red "X", can can instead generate more spam messages or potentially initiate a download or installation of a virus.
- If you encounter fake alerts on websites, do not use your mouse to close them.
- Microsoft Windows users can close them with the keyboard shortcut: Alt + F4
- Apple Macintosh users can close them with the keyboard shortcut: Command + Q
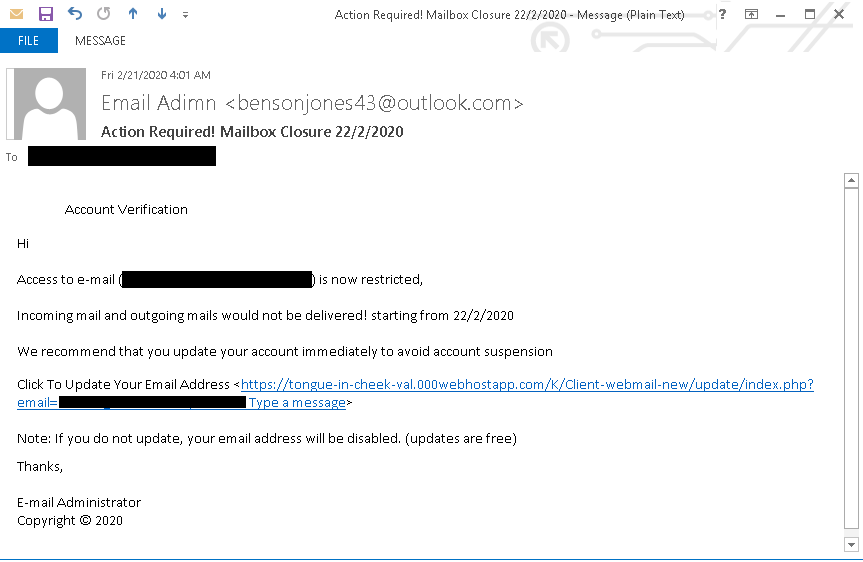
- Fake alert message can also come through email, as illustrated in the screenshot below.
- Fake alert messages can also come through email.
- Do not reply or click on the links provided.
- If you are not sure if a message is legitimate, contact your company's technical support team.
Protecting Yourself from Malware
There are steps you can take to protect yourself from malware. The following are essential actions you can take to greatly increase your security posture and minimize your potential of becoming a victime of a cyber attack.
- Install an anti-virus/anti-malware software.
- Ensure your operating system and software are up-to-date with the latest updates. Updates often contain security and vulnerability patches.
- Use login accounts with limited privileges rather than "administrator" accounts. This limits access to your system in the event a malware infects your computer.
- Keep a daily backup copy of your important documents on a separate USB or network hard drive. Alternatively, a cloud backup will work as a great offsite copy.
- Do not click on unfamiliar links, email attachments, or install software from unknown sources.
Popular antivirus and security solutions for your computer. Click on the Amazon affiliate links below to learn more.
5. Types of Hackers
Hackers typically have a negative connotation is people's minds. What comes to mind is someone who illegally breaks into systems to steal information. However, there are many classifications of hackers, some good and some bad.
- Black Hat - These are the skilled, malicious, bad guys that break into systems to illegally procure information or cause destruction
- White Hat - These are the skilled, good guys that break into systems, with full permission from the organization, in order to find security weaknesses so they can be remedied by the organization.
- Gray Hat - Skilled hackers that sometimes breaks into systems illegally, without permission. Unlike a black hat, their intent is not malicious. They will typically alert the company the hacked directly before making their findings public. If the company shows disinterest in fixing their security issues, the hacker may threaten to make the information public, forcing the company into remedying a security vulnerability.
- Suicide Hacker - An individual who hacks into a system knowing they will likely be caught.
- Script Kiddie - This is a term used for unskilled hackers who take advantage of tools, created by skilled hackers, to carry out their attacks.
- Cyber Terrorist - A skilled hacker motivated by political or religious beliefs.
- State Sponsored Hacker - A skilled hacker employed by a government in order to break into a foreign government's systems.
- Hacktivist - A hacker, usually driven by a political agenda, who's goal is to defame or embarrass a target.

6. Public Wi-Fi Networks
Public wireless networks such as those found in coffee shops, hotels, airports and other public places are often not secure. They are set up with ease-of-use and convenience in mind, but not security.
There is an increased risk of your information being intercepted by someone else. Extra precaution should be used when connecting to a public network.
- Ensure the Wi-Fi has password protection using WPA2 encryption. Never connect to an unsecured, open, public Wi-Fi.
- Avoid connecting to networks using WEP or WPA encryption. These have been compromised and are easily cracked.
- Use a reliable VPN service as soon as you join a public network. This further encrypts the data sent from your device.
- Send sensitive data over secure (HTTPS) websites.
7. Two-Factor Authentication (2FA)
- Two-Factor Authentication (2FA), also known as multi-factor authentication, provides an extra layer of authentication.
- It combines the security of "what you know" (e.g., your password) with "what you have" (e.g., smartphone).
- If your user ID and password are stolen, the perpetrator will not be able to access your account without your smartphone.
- Two-factor is enabled on many of our systems, or other company systems that we use, for added security.
8. Complex Password
Passwords are key component to restrict access to your systems and data. It's important to ensure you follow best practices when creating your password. This includes employing password complexity, length, change cycle, and history. You may consider creating a 'passphrase' instead of a password to help make remembering it easier. Follow these recommendations to help ensure you have a strong password so that a cyber bad guy cannot easily guess or hack.
- Make it complex by using:
- Upper- and lower-case letters
- Numbers
- Symbols (such as: $ @ ! ^)
- Replace the letter "o" with a "0" (zero), or the letter "E" with a "3"
- Passphrase instead of password
- Make it a minimum of eight (8) characters, using at least one number and one symbol
- An 8-character password has 645 trillion combination
- Do not incorporate personal information (e.g., name, account #, birthday)
- Do not reuse your past six (6) passwords
- Do not share your password
- Do not leave your password in an unsecure place, such as on a piece of paper under your keyboard
- Do not use simple words or patterns such as 'password' or '12345678'
- Some systems will remind or force you to change your password after a predefined amount of time (e.g., 90 days). If a system does not offer this feature, manually change it yourself every 90 days.
In 2023, the five (5) most common passwords revealed from hacks as reported by cybernews.com were:
- 123456
- 123456789
- qwerty
- password
- 12345
Don't get hacked, secure your passwords with LastPass, a secure online password manager.
The amount of time to crack a password using a typical household computer, as reported by https://howsecureismypassword.net:
- "password" = seconds
- "MyStrongPa$$w0rd!" = 93 trillion years
Between 1960 and 1977 the secret code allowing U.S. Presidents to launch nuclear missiles was 00000000, as reported by http://qi.com/infocloud/passwords
Back to Top9. USB Hacking
Your device's USB ports can be vulnerable to attacks. You should never plug anything into your USB port that you have received from an unknown person or source. This includes charging cables.
- Malicious USB sticks or cables have software implanted inside them.
- Bad guys bypass security restrictions by having the USB think a keyboard or mouse was plugged in.
- Never accept or plug anything into your USB ports unless the source is reputable.
- Never plug any USB cable or device you find on the streets or in public spaces. These devices many be implanted with malware and intentionally "lost."
- Buy USB devices and cables from reputable sources. You should be wary when you see a USB charging cable selling on eBay for $2.99 when it typically costs $29.95 in most box stores.

10. Juice Jacking
Juice Jacking is an attack against the charging port of your device. Most mobile devices have a charging port that also double as a data connection. An attacker could exploit your device by setting up a malicious charging station that takes advantage of the data connection of your charging port. Here are a few tips to avoid Juice Jacking attacks:
- Top off your battery at home or work
- Carry a personal outlet charger
- Carry a backup battery
- Lock phone while charging
- Ensure you set a PIN/password
- Power off your phone before charging
- Purchase a "power only" USB cable
- Never charge your phone using a third-party system - such as charging stations those found at airports or other public kiosk
11. SIM Swapping/Hi-jacking
A type of fraudulent account takeover exploiting a mobile phone carrier's weak internal processes of moving your telephone number to another device.
Criminal gathers enough personal information about a you to create a false identity. They impersonate you and call your provider and claim your SIM card is lost/damaged. Your phone number then is transferred to the perpetrator's SIM card.
Perpetrator can then receive your calls, emails, and text messages.
How to Protect Yourself from SIM Swapping
- Put a password on your mobile phone and account.
- Ensure your phone has adequate anti-virus protection.
- Download apps from known and trusted sources.
- Do not readily give out personal information over the phone.
- Do not reveal too much personal data on social media or other online applications.
- Call your provider and ask if SIM cards have been issued without your knowledge.
- Never ignore an SMS/email alert about a SIM swap on your account.
- Call your provider to add extra security
- Enabling a secret password or PIN (AT&T, Sprint, Verizon)
- Creating a "care password" (T-Mobile)
Signs to Look for in a SIM Swap Fraud
- Your cell service stops suddenly.
- You receive a message saying your service is transferred.
- Contact your phone carrier immediately if you experience any of these.
- Contact your bank and other companies immediately with whom you have set up your phone to receive security/access codes.
Act Fast!
This is a criminal's backdoor to your bank account.
Perpetrators can drain bank accounts in a matter of minutes.

Aug 8, 2018 - Florida Man Arrested in SIM Swap Conspiracy. Read all about it »
12. Summary
Cyber criminals are constanting trying to scam people of their money, their identity, and their personal data. For businesses and government agencies, cyber criminals also go after their money. But more importantly, it is proprietary research data, state secrets, and other information that can hurt a business or a national that's often the most sought after. Some say it's not "if" I get hack, it is "when." Everyday, people's private data are breached. Some make it to the news, many don't. You can make it harder for scammers and hackers to target you by following these simple and cost effective measures:
- Make sure websites you access is secure with HTTPS when accessing personal data (e.g., bank, emails, payment gateways).
- Encrypt sensitive data when possible.
- Install an reliable antivirus software.
- Avoid clicking on attachments and links in emails you are not expecting.
- Scrutinize popup message and email alerts to identify their legitimacy.
- With a reliable VPN service when on public Wi-Fi.
- Enable two-factor authentication when available on systems and websites you access (e.g., banking, stock trading)
- Create strong passwords or passphrases.
- Don't plug into your computer USB cables, thumb drives, or other devices from unknown sources, such as a USB cable or drives you may find in an airport waiting lounge.
- Don't charge your smartphone using public USB charging stations.
- Call your mobile phone service provider to add extra security to your account by enabling a secret or card password.
13. External Reference
- Never forget a password with LastPass Online Password Manager
- Learn more about ransomware at McAfee
- Microsoft virus alert scam - https://www.bleepingcomputer.com/virus-removal/remove-virus-alert-from-microsoft-tech-support-scam
- Online hash generator tool - http://www.miraclesalad.com/webtools/md5.php
- How secure is my password? - https://howsecureismypassword.net/
- Florida Man Arrested in SIM Swap Conspiracy - https://krebsonsecurity.com/2018/08/florida-man-arrested-in-sim-swap-conspiracy/
- Hancock Health suffered a ransomware attack - https://www.zdnet.com/article/us-hospital-pays-55000-to-ransomware-operators/
- Ransomware Freezes Eight Years of Police Evidence - https://www.bankinfosecurity.com/ransomware-freezes-eight-years-police-evidence-a-9664
- 10 Most Hacked Passwords Revealed in 2019 report - https://www.foxbusiness.com/technology/most-hacked-passwords-2019



