Table of Content

What is Malware?
Malware is a generic term for bad software. The word malware comes from the words malicious and software.
Although there is no official breakdown, we can divide malware into several broad categories of malware: adware, spyware, hijackers, toolbars, and others. Many, if not most malware programs will fit into more than one category. It is very common for people to use the words adware, spyware, and malware interchangeably. Most products that call themselves spyware or adware removers will actually remove all types of malware.
Malware can be present on any website or software that contains malicious code or downloads. There are a few common sources where malware is the most prevalent:
- Spam email
- Gambling websites
- Sites offering free games and software
- Adware is the most common type of malware from these sites
- Adult-content websites
- Embedded advertisements (banner ads, popups)
- Unpatched software vulnerabilities
- Ensure your software and operating system (Windows, OSX) have the most up-to-date patches installed
In this article, we'll briefly describe each of the various types of malware.
Back to TopAdware
Adware is the class of programs that place advertisements on your screen. These may be in the form of pop-ups, pop-unders, advertisements embedded in programs, advertisements placed on top of ads in web sites, or any other way the authors can think of showing you an ad. The pop-ups generally will not be stopped by pop-up stoppers, and often are not dependent on your having Internet Explorer open. They may show up when you are playing a game, writing a document, listening to music, or anything else. Should you be surfing, the advertisements will often be related to the web page you are viewing.
Back to TopDialers
Dialers are programs that set up your modem connection to connect to a 1-900 number. This provides the number's owner with revenue while leaving you with a large phone bill. There are some legitimate uses for dialers, such as for people who do not have access to credit cards. Most dialers, however, are installed quietly and attempt to do their dirty work without being detected.
Back to TopSpyware
Programs classified as spyware send information about you and your computer to somebody else. Some spyware simply relays the addresses of sites you visit or terms you search for to a server somewhere. Others may send record your keystrokes and back information you type into web forms or the names of files you download. Still others can search your hard drive and report back what programs you have installed, contents of your email software address book (usually to be sold to spammers), or any other information about or on your computer - such as your name, browser history, login names and passwords, credit card numbers, and your phone number and address.
Spyware often works in conjunction with toolbars. It may also use a program that is always running in the background to collect data, or it may potentially integrate itself into your web browser, allowing it to run undetected whenever you go onto the Internet.
Back to TopHijackers
Hijackers take control of various parts of your web browser, including your home page, search pages, and search bar. They may also redirect you to certain sites should you mistype an address or prevent you from going to a website they would rather you not, such as sites that combat malware. Some will even redirect you to their own search engine when you attempt a search. Hiijackers often target a specific web browser cause of a vulnerability they can exploit.
Back to TopToolbars
Toolbars plug into Internet Explorer and provide additional functionality such as search forms or pop-up blockers. The Google and Yahoo! toolbars are probably the most common legitimate examples, and malware toolbars often attempt to emulate their functionality and look. Malware toolbars almost always include characteristics of the other malware categories, which is usually what gets it classified as malware. Any toolbar that is installed through underhanded means falls into the category of malware.
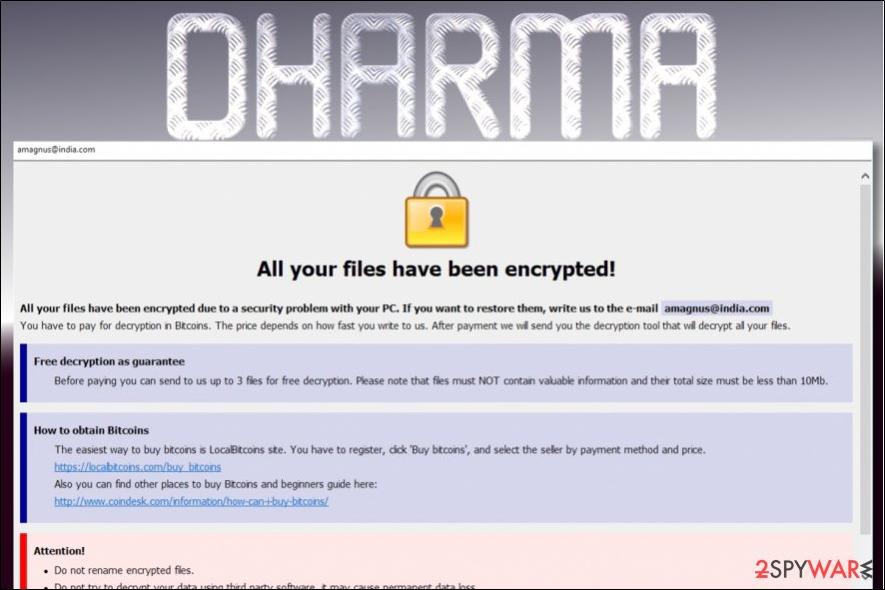
Back to TopRansomware
A type of malware that encrypts all of your personal files and holds them hostage, and they have been around since the late 1980s. They will provide you with a password to decrypt your files after you have paid the ransom, usually in the form of cryptocurrency such as Bitcoin since it is not traceable. Prior to cyptocurrency, payment was sent via snail mail.
Virus
Malware that replicates itself when executed by modifying code in other computer programs on your system. Used to bring systems offline by corrupting data and causing system failure.
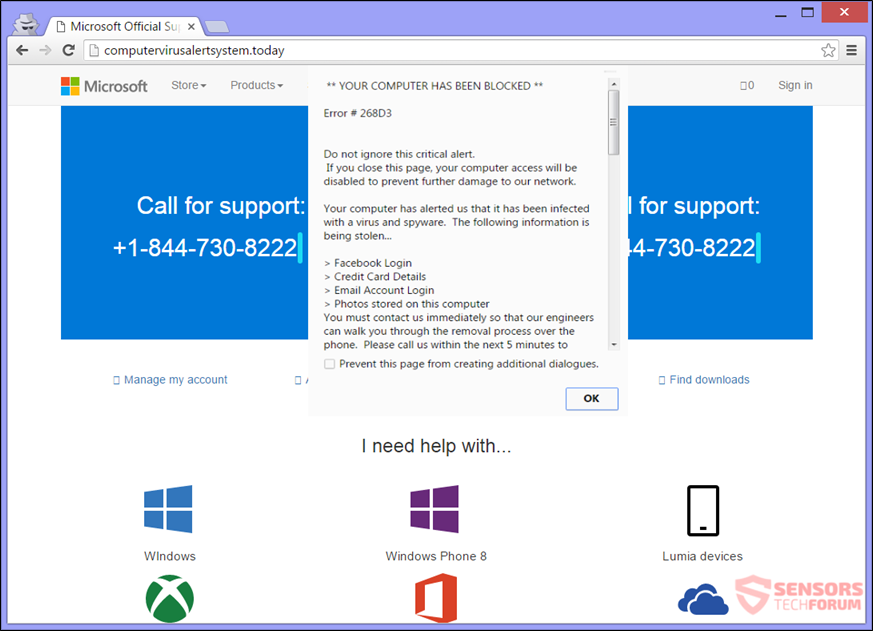
Back to TopVirus Alert Scam
Malicious websites or advertisements may redirect your web browser to a fake "virus alert" page. This page produces warnings saying your computer is infected, and gives you a number to call. If called they will attempt to have you give them control of your device, as well as send them money for their virus removal "services".
Back to TopWorms
Similar to a virus, spreads throughout devices corrupting data and bringing network systems offline. Unlike a virus, worms can be spread without being executed by the user.
What to do to Protect Yourself?
The easiest way to protect yourself, your computer, and your files is to purchase a security software (e.g., anti-virus software). Most will work behind-the-scene to protect your computer and will alert you when it detects something malicious. There are new types and variants of malware and viruses practically on a daily basis. It is important to remember to always keep your security software up-to-date to make sure you are protect from the latest threat. Most will automatically do this for you while some may require action on your part.
The list below are some reputable anti-virus software to consider. Click on the Amazon affiliate links below to learn more.
- Bitdefender Antivirus Plus
- ESET NOD32 Antivirus
- Norton 360 Deluxe
- McAfee Total Protection
- Avast Premium Security
- Malwarebytes Anti-Malware Premium 3.0